This article covers the steps necessary to configure the SSL settings for a cluster. SSL settings for a cluster are optional when you initially create a cluster and can be done later after the cluster has been created.
If the database server requires SSL, check the box to enable SSL for the cluster. You will need to provide a server certificate and Server Key to ScaleArc. The SSL certificate must be signed by a CA (Certificate Authority) that is already approved by the application hosts for it to be accepted.
If the SSL setting is disabled, ScaleArc negotiates down LOGIN encryption for client connections. Unlike SQL Server, ScaleArc for MySQL does not auto-generate a self-signed SSL certificate. This happens in authentication offload ON mode only.
Note: ScaleArc supports TDS over SSL.
Follow these steps to configure cluster SSL settings:
- Click the CLUSTERS tab > Add Cluster button on the ScaleArc dashboard.
- Locate SSL Settings on the screen. This is the fourth panel on the Create Cluster screen.
- Select the SSL Authentication Offload checkbox to show the SSL Settings screen.
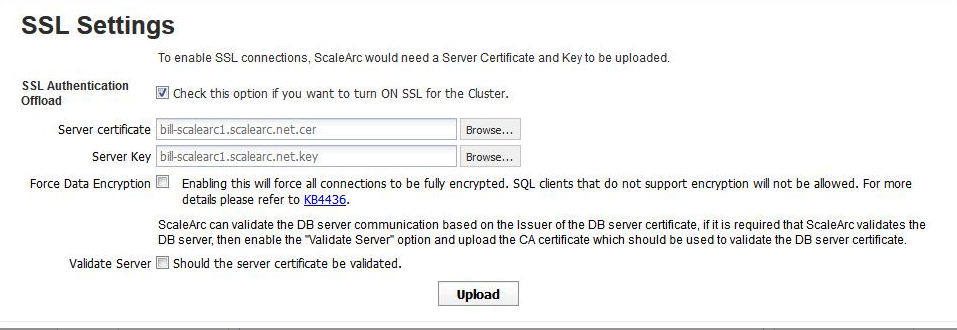
-
Configure the fields as follows:
Field/Button Description Default/User input SSL Authentication Offload SSL Authentication Offload allows you to establish secure communication between the client and the server via ScaleArc.
ImportantAs a prerequisite, if a SQL client needs to initiate full encryption with ScaleArc's SSL enabled cluster, ScaleArc's inbound IP should be reverse-resolvable to the hostname entry in the certificate uploaded on the ScaleArc cluster. Any modification to the SSL Authentication Offload requires you to restart the cluster.
Select the checkbox. Server certificate Requires a Server certificate as a prerequisite. The SSL Certificate must be generated by a CA-Authority that is already approved by the application hosts, for it to be accepted by them. All certificates should be in the PEM format. Browse to locate and attach the appropriate Server certificate. Server Key Requires a Server Key as a prerequisite. Key-related files must be in PEM format. Browse to locate and attach the appropriate Server Key. Force Data Encryption Forces all connections to be fully encrypted. SQL clients that do not support encryption will not be allowed.
Select the check box to activate. Validate Server Allows ScaleArc to validate the DB server communication and upload the appropriate CA certificate.
Select the check box to activate. Upload Uploads the attachments. Note that re-uploading or replacing an existing SSL cert requires a cluster restart. Click to complete the upload.
SSL and Force Encryption
The following tables show how ScaleArc handles client connections with different encryption requests in both Force Encryption ON and OFF modes. Modifying the Force Data Encryption setting does not require a cluster restart.
Force Encryption switch OFF
|
Client Encryption request
|
ScaleArc behavior
|
ScaleArc request to the server on behalf of a client (same as requested by client) |
|---|---|---|
| Encryption not supported. | Does not do SSL encryption for this connection. |
Requests no encryption. If the server is configured to force full channel encryption, it will fail the connection. |
| Encrypt Login only |
ScaleArc does SSL handshake and accepts encrypted login |
Request Login only encryption. If the server is configured to force full channel encryption, it will fail the connection. |
| Requests full channel encryption | Replies that it supports it. | Request for full channel encryption. |
Force Encryption switch ON
|
Client Encryption request
|
ScaleArc behavior
|
ScaleArc request to the server on behalf of a client (same as requested by client) |
|---|---|---|
| Encryption not supported | Replies that encryption is required and closes the connection |
N/A |
| Requests full channel encryption | Replies that it supports it and proceeds. | Request for full channel encryption. |
| Encrypt Login only |
ScaleArc replies full encryption is required and proceeds to do full channel encryption. |
Request for full channel encryption. |