The Authentication Configuration screen allows you to set up and configure the preferred authentication mechanism with which ScaleArc authenticates users.
ScaleArc supports the following authentication types:
- Local user authentication for users who are stored within ScaleArc.
- LDAP authentication for LDAP users over an LDAP server.
- Third-party authentication for authentication scheme over REST APIs.
Local Authentication
When this authentication type is selected, ScaleArc creates and manages users locally.
Note that ScaleArc does not allow the creation of user groups; it only manages individual users.
Follow these steps to set up local user authentication:
- Click on the SETTINGS menu > User Management > Authentication Configuration in the ScaleArc dashboard.
- Select Local Authentication from the drop-down for Authentication type.
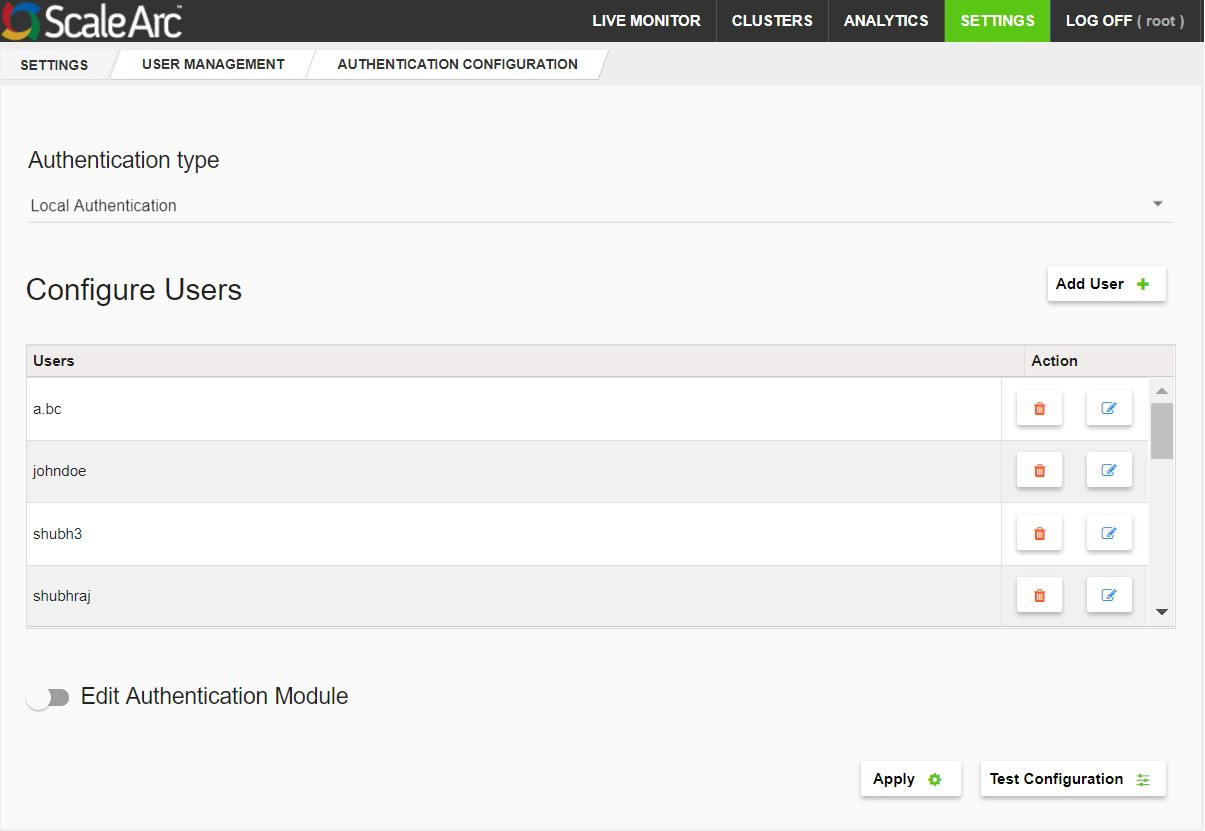
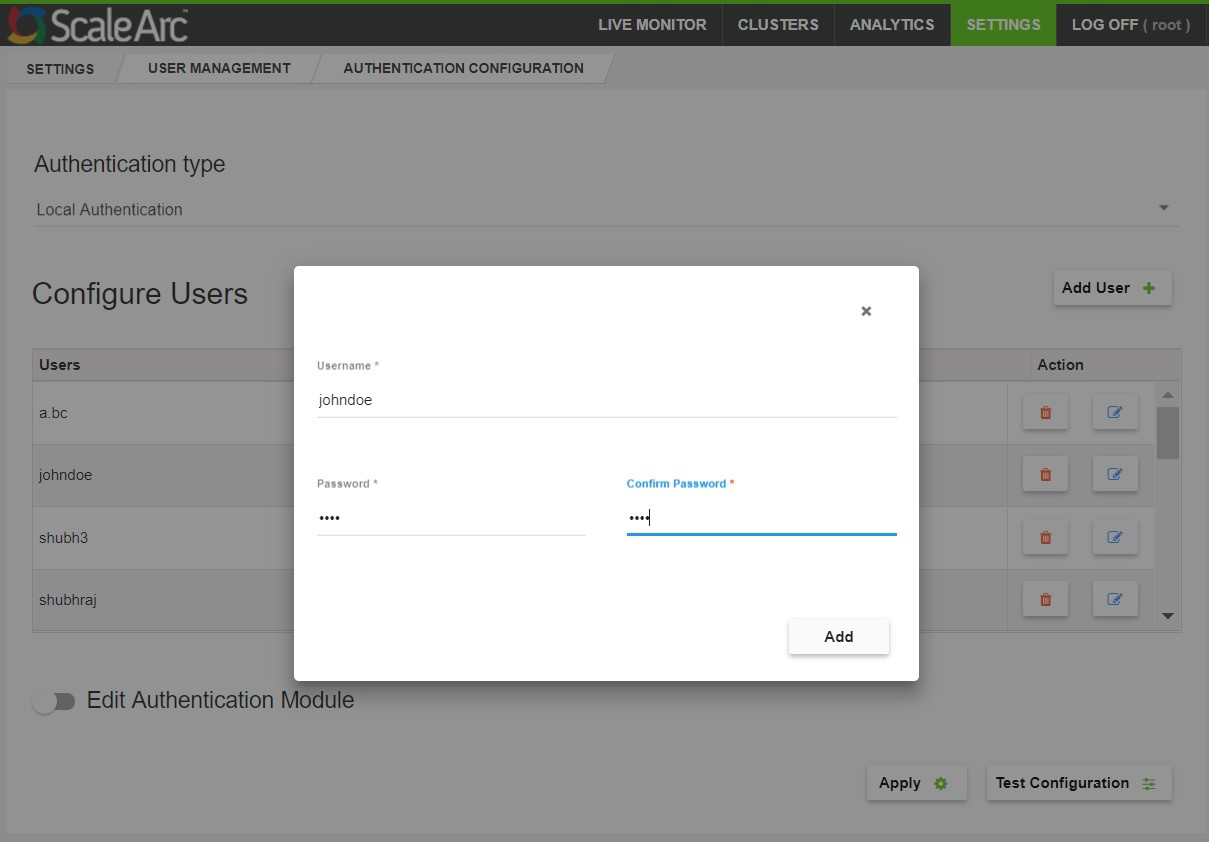
- Click Add User to configure a new user. Enter a username, password, and password confirmation for the user.
- The new user now appears in the Users listing.
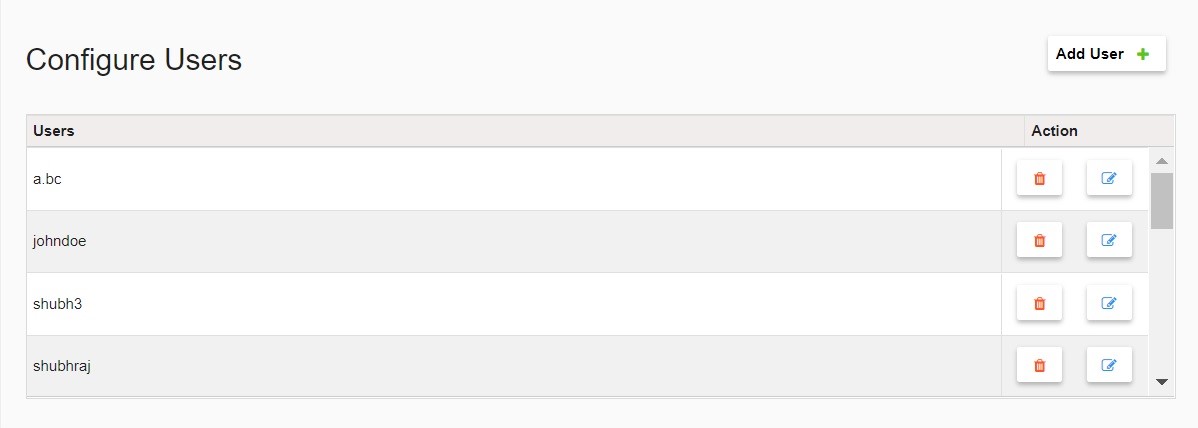
- To remove a user from the list, click on the Delete icon next to the user.
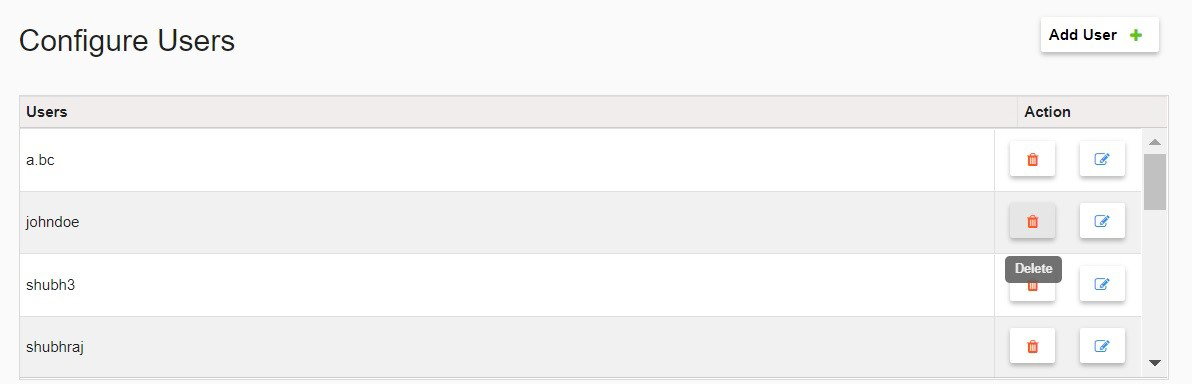
- To change the user's password, click on the Edit User Password icon and follow the prompts.
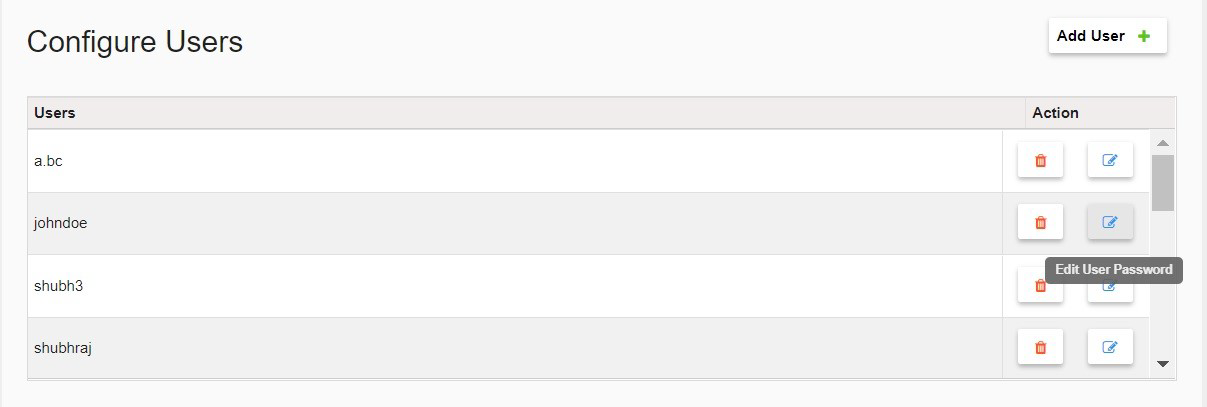
- Review Editing the Authentication Module section to make changes to the module.
- Next, create and/or edit the Authentication Policy and Access Control Configuration.
Authentication over LDAP server
This authentication mechanism allows ScaleArc to connect to an LDAP server over LDAP protocol to authenticate users.
These users and groups are referenced from the LDAP server and do not require to be re-created in ScaleArc.
- Click on the SETTINGS tab > User Management > Authentication Configuration in the ScaleArc dashboard.

- Choose Authentication over LDAP Server from the drop-down for Authentication type.
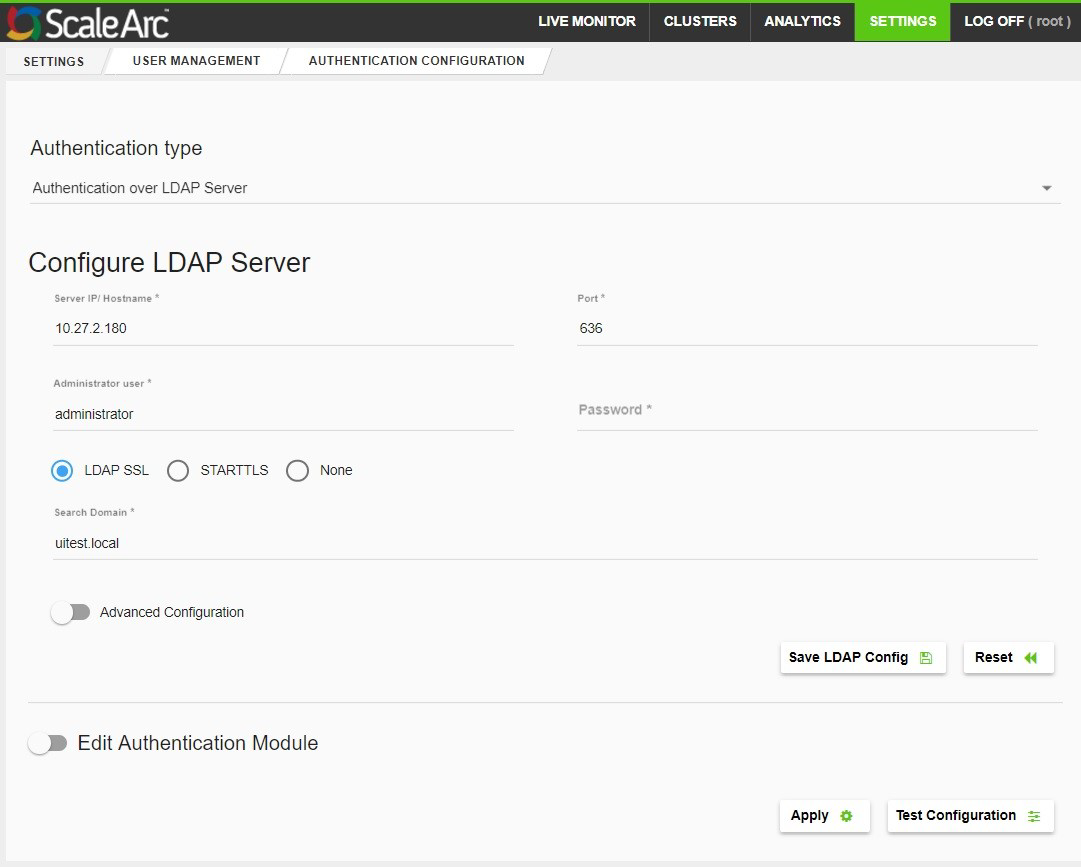
-
Enter the IP/hostname of the LDAP server, port number, administrator username (without domain), and password.
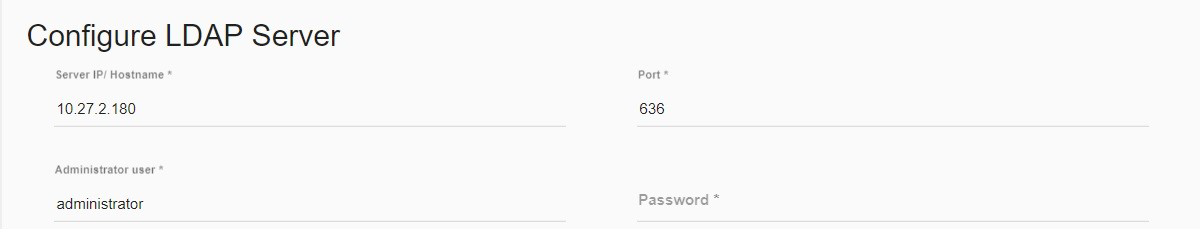
Note: ScaleArc does not check the validity of Administrator username, password or search domain while saving LDAP configuration. If any of the three fields are entered incorrectly, ScaleArc does not allow the newly-configured LDAP server settings to be applied.
If the administrator's account password has an expiration date, the LDAP authentication from ScaleArc will fail past the expiration date. In this situation, the user needs to log into ScaleArc via the root user account and change the administrator password using the LDAP config page in ScaleArc. To avoid failure, update your administrator's password in ScaleArc when the password expires. - Select if you wish to communicate over LDAP SSL, STARTTLS, or neither. If you select STARTTLS, the first authentication will be over non-SSL.
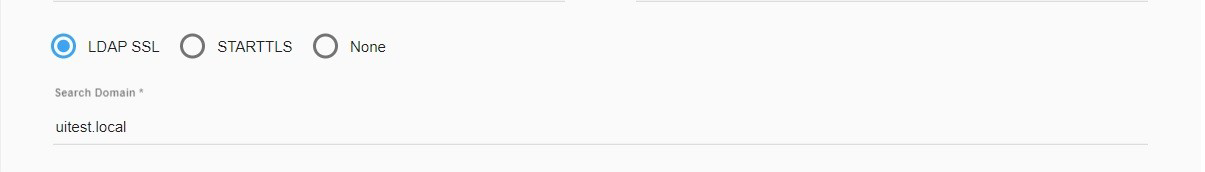
- Enter the Search Domain (for example, testqa.local). This optional parameter is used only when a configured search domain is being used as a domain source.
- Select Advanced Configuration (optional) for configuring user and group filter attributes for LDAP binding. If you choose to use this option:
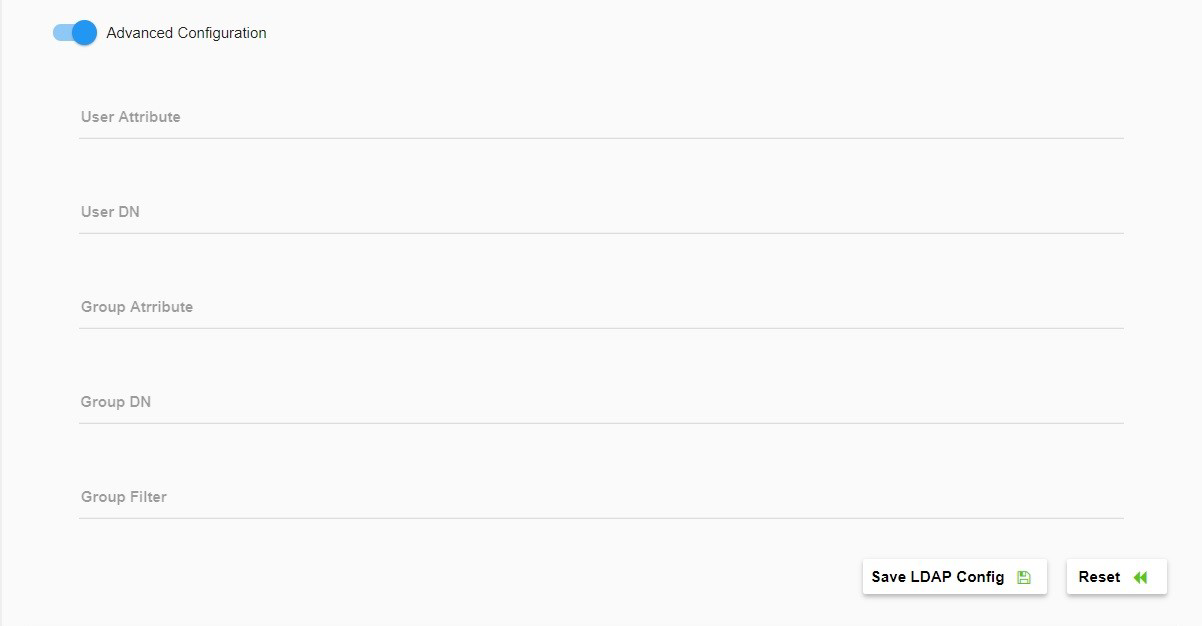
Use the toggle to Enable Advanced Configuration then configure as follows:Field Description Default/User input User Attribute Attribute matches the username passed during authentication.
Examples: sAMAccountName, cn, uidUser DN Base domain name under which to perform user search.
Example: ou=Users,dc=example,dc=comGroup Attribute LDAP attribute to follow on objects returned by group filter in order to enumerate user group membership. Examples: For group filter queries returning group objects, use: cn. For queries returning user objects, use: memberOf. The default is cn.
Enter the appropriate string. This is an optional setting.Group DN LDAP search base to be used for group membership search. It can be the root containing either groups or users. For example: ou=Groups, dc=example, dc=com. Enter the appropriate string. This is a required setting. Group Filter A template used when constructing the group membership query. The template can access the following context variables: [UserDN, Username].
To support nested group resolution for Active Directory, use the following query: (&(objectClass=group)(member:1.2.840.113556.1.4.1941:={{.UserDN}})).The default is: (|(memberUid={{.Username}})(member={{.UserDN}})(uniqueMember={{.UserDN}})), which is compatible with several common directory schemas. - Click Save LDAP Config to save the configuration.
- Review Editing the Authentication Module section to make changes to the module.
- Next, create and/or edit the Authentication Policy and Access Control Configuration.
Authentication with 3rd party
ScaleArc offers the ability to authenticate against a third-party REST API-based authentication server like HashiCorp Vault. The following instructions provide steps for authenticating users against HashiCorp Vault:
- Click on the SETTINGS menu > User Management > Authentication Configuration in the ScaleArc dashboard.

- Choose Authentication with 3rd party from the drop-down for Authentication type.
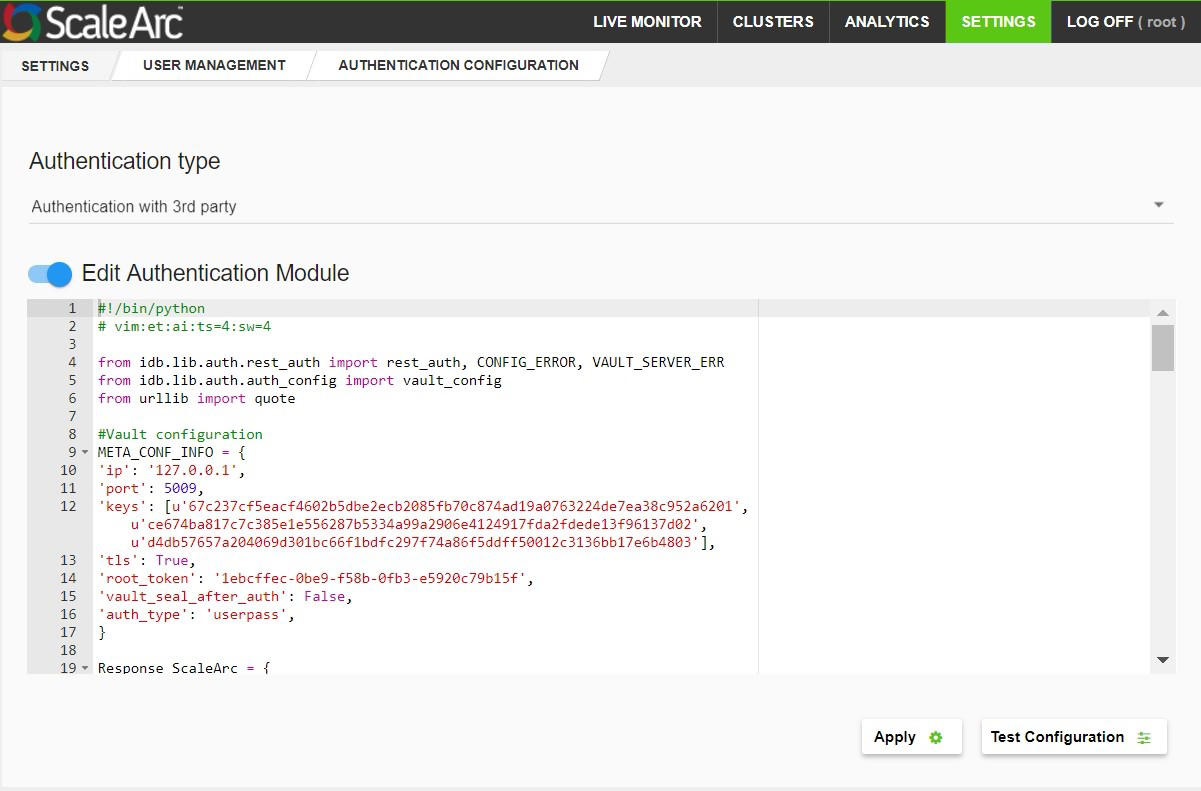
- Use the toggle switch to Enable the Edit Authentication Module.
- Edit the META_CONF_INFO inside the code to reflect your HashiCorp vault server settings, IP, port, keys, TLS setting, root_token, and the auth_type.
- If you want to seal your HashiCorp Vault server after each of the authentication requests is performed, set the vault_seal_after_auth parameter to True.
- Click Test Configuration when done to test the edited authentication module. Enter a valid username/password to test this authentication module.
- Click Apply when done. Enter a valid username/password to validate this authentication and save and apply it as the authentication module for ScaleArc.
- Review Editing the Authentication Module section to make changes to the module.
- Next, create and/or edit the Authentication Policy and Access Control Configuration.