ScaleArc recommends a High Availability (HA) deployment of two ScaleArc appliances in order to provide uninterrupted operation that would otherwise occur when ScaleArc is running as standalone and became unavailable.
Configure one of the appliances in the pair as the primary node and the other as the secondary node. The primary node accepts connections and manages servers while the secondary node monitors the primary. In case the primary is unable to accept connections, the secondary node takes over.
This article describes how to configure High Availability for ScaleArc. ScaleArc uses the pacemaker module from ClusterLabs to setup high availability and supports active-passive peer configuration, with active resource sync between two nodes, virtual IP migration, and node failure detection.
- Doing an HA linkup first allows the domain Join operation to occur only once on the HA primary, requiring the HA secondary to join the domain first. Once this has successfully completed, the HA primary joins. The result is simpler and less error-prone because it forces all the AD configuration on the HA pair to be identical.
- If you are configuring Kerberos for user management, set up delegation on both the machines (primary and secondary).
- The virtual IP address technology used in the ScaleArc HA feature is not compatible with most cloud services. For instructions on HA configuration in the various cloud services, consult the installation section for specific instructions on setting up ScaleArc HA on your cloud service.
Prerequisites
Before you begin, ensure the following:
- Both ScaleArc systems have the same hardware/VM configuration.
- Both ScaleArc systems have the same license parameters.
- Each ScaleArc appliance has a unique license key.
- Configure virtual IP (VIP) prior to configuring HA.
- The network configuration on both the ScaleArc systems should be similar. This will ensure that whenever a HA switchover occurs, the other node is able to host all VIPs and handle all network communication.
Add a secondary node
The following section guides you to add a secondary ScaleArc appliance to the already installed standalone primary ScaleArc appliance.
-
Click on the SETTINGS menu tab > HA Settings on the ScaleArc dashboard from the primary node in the HA pair.
Important: Make sure the Inbound/Outbound IP addresses are using a virtual IP configuration.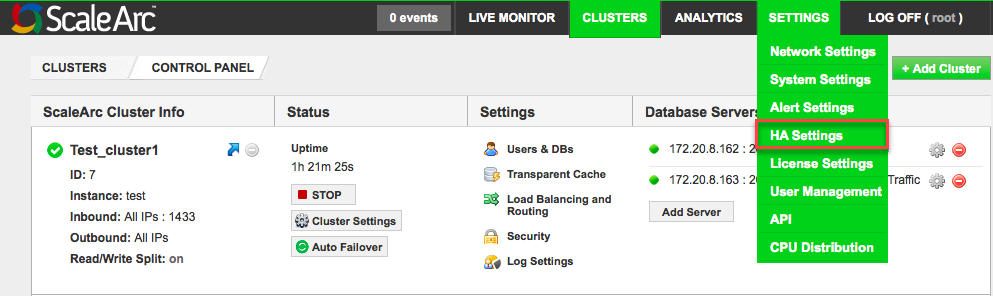
-
Configure High Availability (HA) as follows:
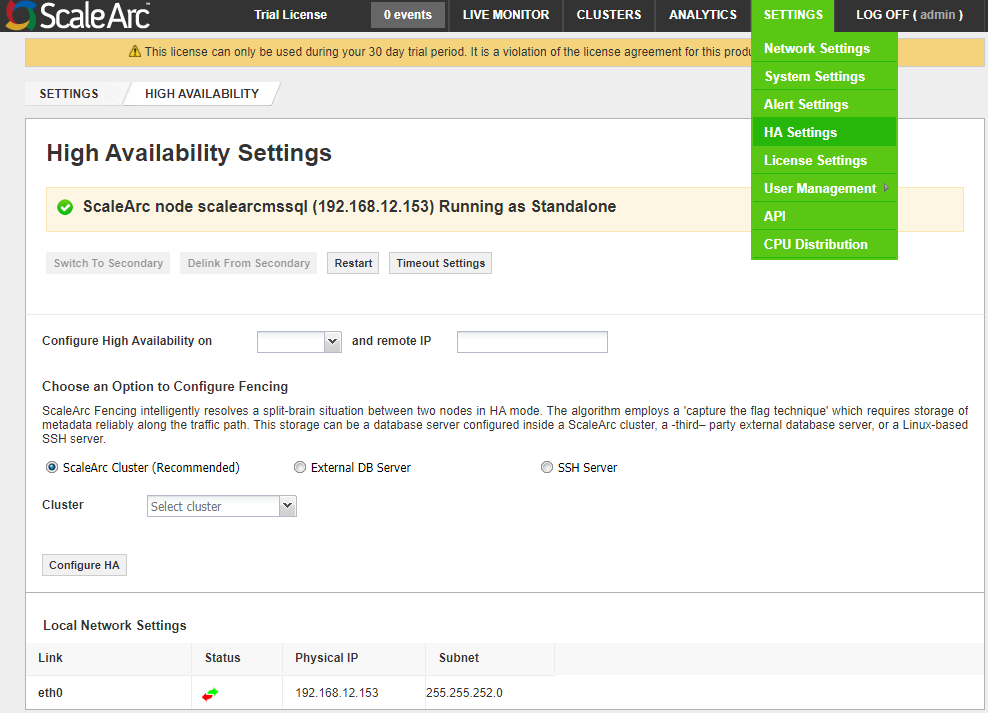
Field/Button Description Default/User input Configure High Availability on The drop-down list of the active network interfaces associated with the ScaleArc appliance. Refer to the section labeled Local Network Settings at the bottom of the page to view the available network interfaces. Select a network interface. remote IP address The remote IP address for the selected network interface. Enter the remote IP address used for HA. -
Select a fencing option. The fencing device is a component of a ScaleArc high availability cluster that monitors and cuts off access to a resource (VIP’s, core engine) from a node in the cluster if it loses contact with the rest of the nodes in the cluster. ScaleArc Fencing intelligently resolves a split-brain situation between two nodes in HA mode. The algorithm employs a 'capture the flag technique' which requires the storage of metadata reliably along the traffic path. This storage can be a database server configured inside a ScaleArc cluster, a third-party external database server, or a Linux-based SSH server.
If you selected the recommended fencing option, ScaleArc Cluster:Field/Button Description Default/User input ScaleArc Cluster (Recommended) ScaleArc uses the Read/Write server in the selected cluster to store fencing information. This choice creates a new, logical database on the server. We recommended this approach as it is in line with the traffic flow and helps resolve a split-brain situation accurately. Select this radio button. Cluster A drop down of clusters on the ScaleArc appliance. Select the cluster from the drop-down. Note: As a best practice, witness servers and ScaleArc should be preferably in the same network with low latency for optimal performance. Do not configure ScaleArc primary or secondary machines as the witness server. -
If you selected External DB server as the fencing option, complete as follows:
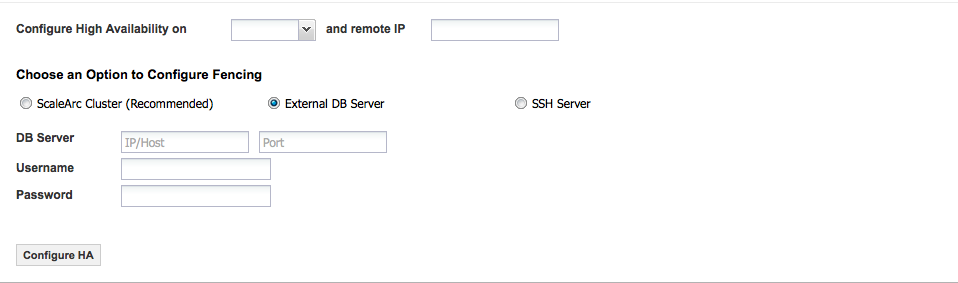 Do not configure the ScaleArc primary or secondary machines as the witness server.
Do not configure the ScaleArc primary or secondary machines as the witness server.Field/Button Description Default/User input External DB Server An external database server (that is not part of any ScaleArc cluster) to store its fencing information. A new logical database is created on this database server to store the fencing information. Select this radio button. DB Server Requires an IP address/Hostname for the selected database server. Enter the database IP/Hostname. Port The server's port. Enter a port number. Username The username to authenticate the external database server. Enter the username. Password The password to authenticate the external database server. Enter the password. -
If you selected the SSH Server fencing option, complete as follows:
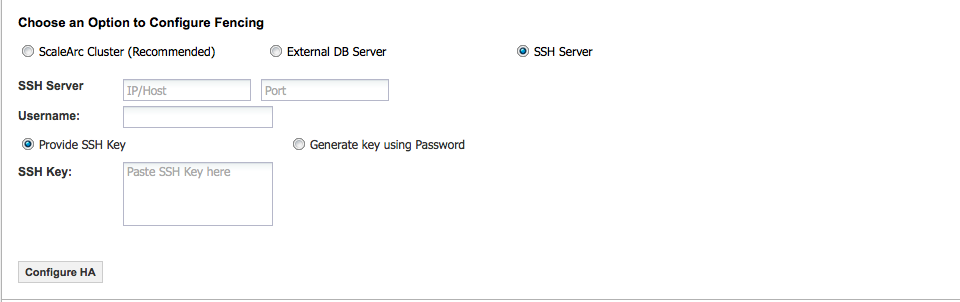
Field/Button Description Default/User input SSH Server SSH access to any Linux based server to store fencing information. This information is stored in files and does not require privileges on the SSH server. 1 Select this radio button. 2 Enter the SSH server's IP/Hostname. Port The server's port. Enter a port number. Username The username to authenticate the SSH server. Enter the username. Provide SSH Key The SSH key used to authenticate to the SSH server. 1 Select this radio button. 2 Enter the SSH key. Generate key using password ScaleArc will generate keys and sync them to the server using the password provided, after which all communication with the server will happen using the generated keys. This password is not saved.
1 Select this radio button. 2 Enter your password. -
Click the Configure HA button to save the configuration.
If you have hosted ScaleArc on a virtual machine, refer to this KB article for configuration requirements specific to virtual environments.
Timeout Settings
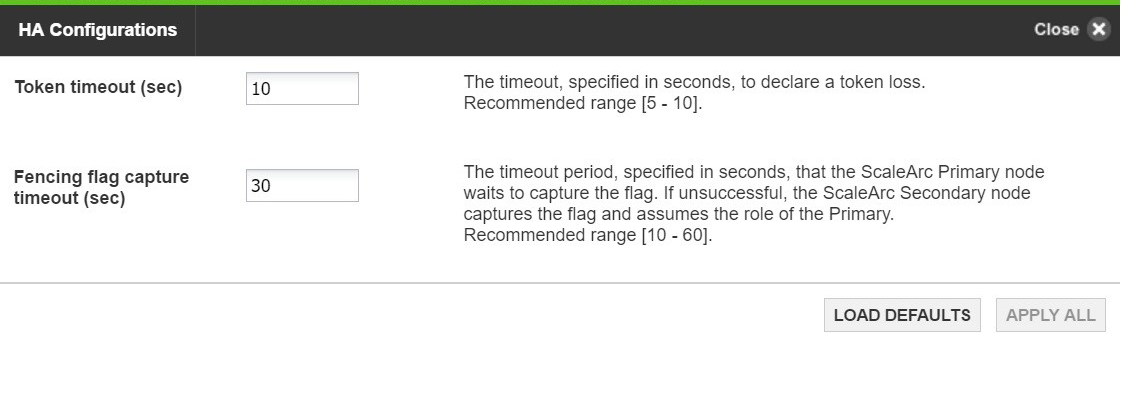
These settings determine the interval before a token can be declared as lost or an HA partner as inactive/dead.
- Click on the Timeout Settings button.
-
Enter the timeouts interval as follows:
Field/Button Description User input/Default Token Timeout (milliseconds) Token timeout is the time, in milliseconds, during which the Corosync token is transmitted around the ring. When this timeout expires, the token is declared lost. ScaleArc recommends 10 milliseconds.
Enter a timeout period. Default is 10 milliseconds. Fencing Flag Capture Timeout The maximum amount of time a HA partner waits before it declares the other partner dead and acquires its resources. Enter a time interval. Default is 30 milliseconds.
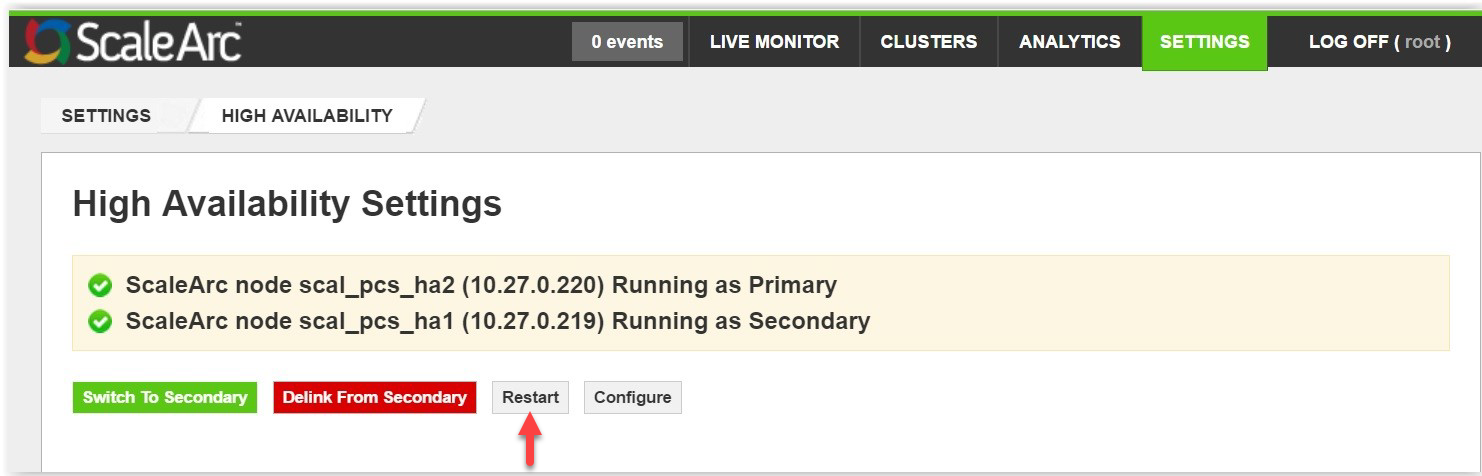
Restart HA service
This action should be initiated only if there are issues with the ScaleArc HA service.
Click on the Restart button to restart the HA service.
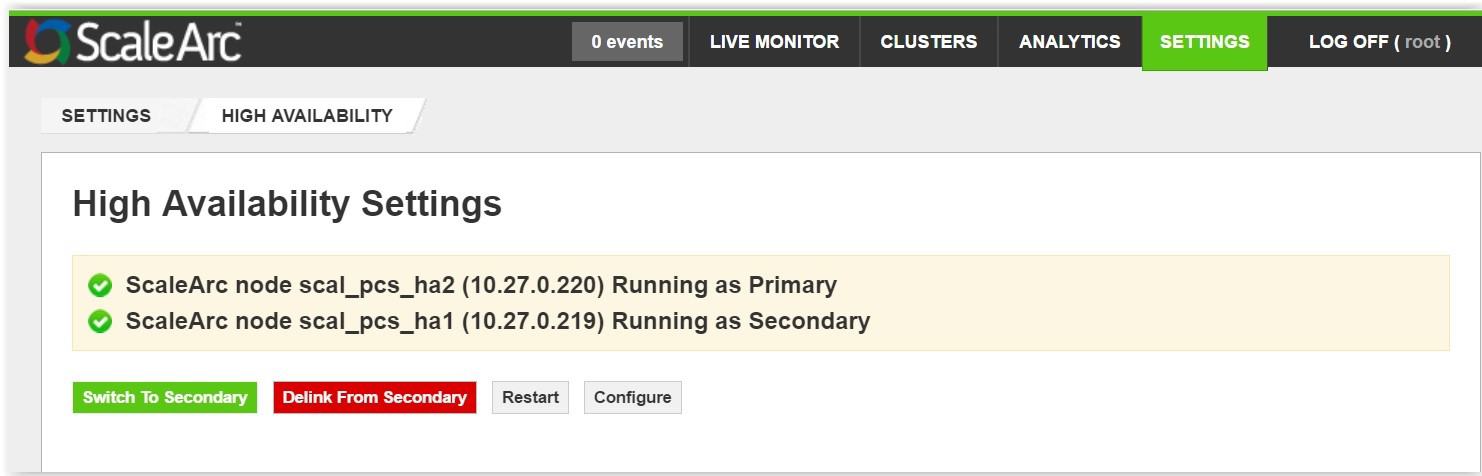
Switch HA roles
Once ScaleArc is in an HA mode, you can perform these actions on the Primary:
-
Delink From Secondary. This will perform HA delink operation and both nodes will become standalone. All the configuration post delink will only be available in primary and secondary will have an empty configuration.
All VIPs will point to the Primary machine.Note: When you delink the ScaleArc appliances, especially when the secondary appliance is down, you must unplug the secondary appliance and perform a factory reset before bringing it up, to prevent IP conflicts and configuration issues. If you have configured Kerberos and wish to delink, set the SPN again for the machine that is running as the primary. - Switch To Secondary.
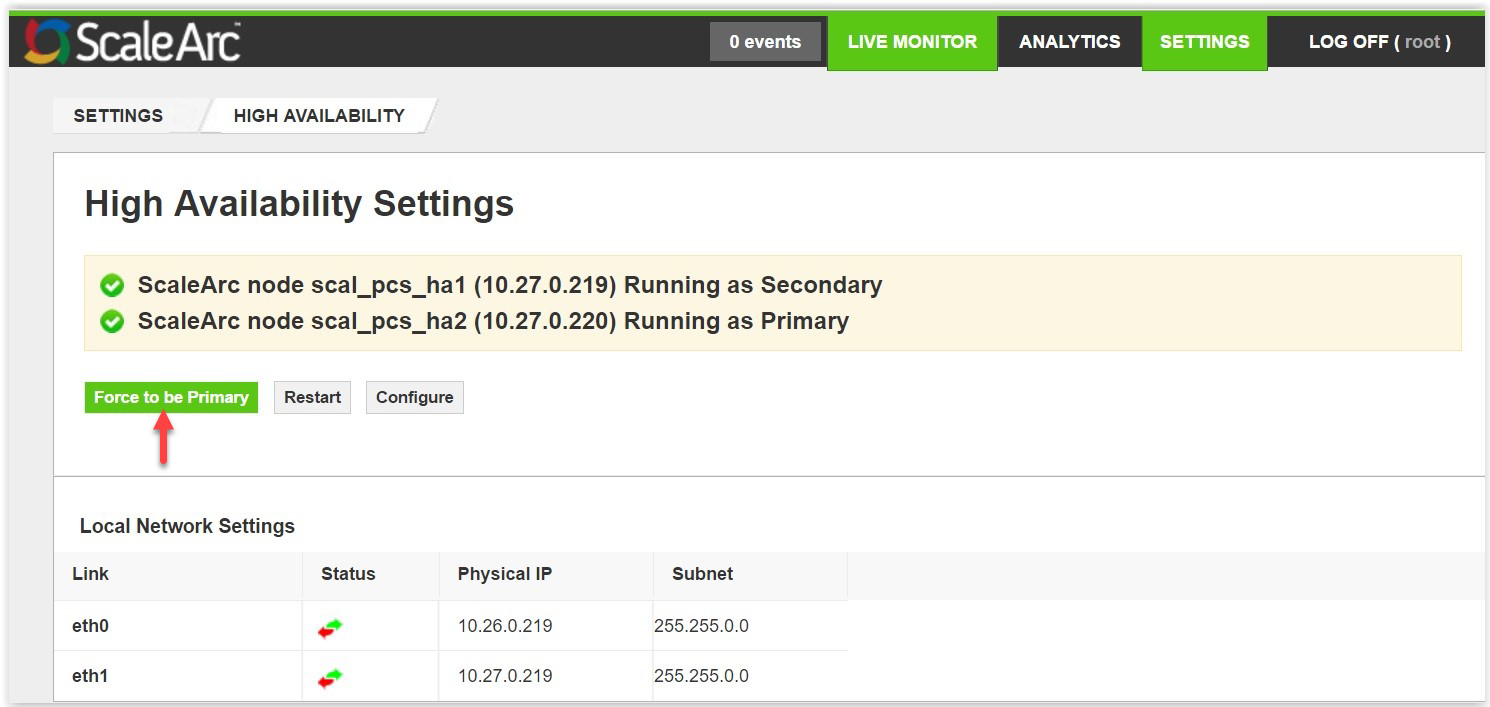
You can perform similar actions on the secondary appliance as outlined below:
- Click on Force to be Primary button to switch the secondary node to become Primary.
Set up HA in the cloud
You can set up an Active-Active HA configuration using an external TCP load balancer.
The configuration steps for this setup depend on the cloud provider as described below: