Overview
LDAP can be used to offload authentication to another service instead of ScaleArc managing logins locally while logging in through the UI.
Information
There are no known issues in a ScaleArc installation integrated with LDAP and can be configured from Settings > User Management > Authentication Configuration. This KB article has more information on how to setup LDAP for authentication with ScaleArc.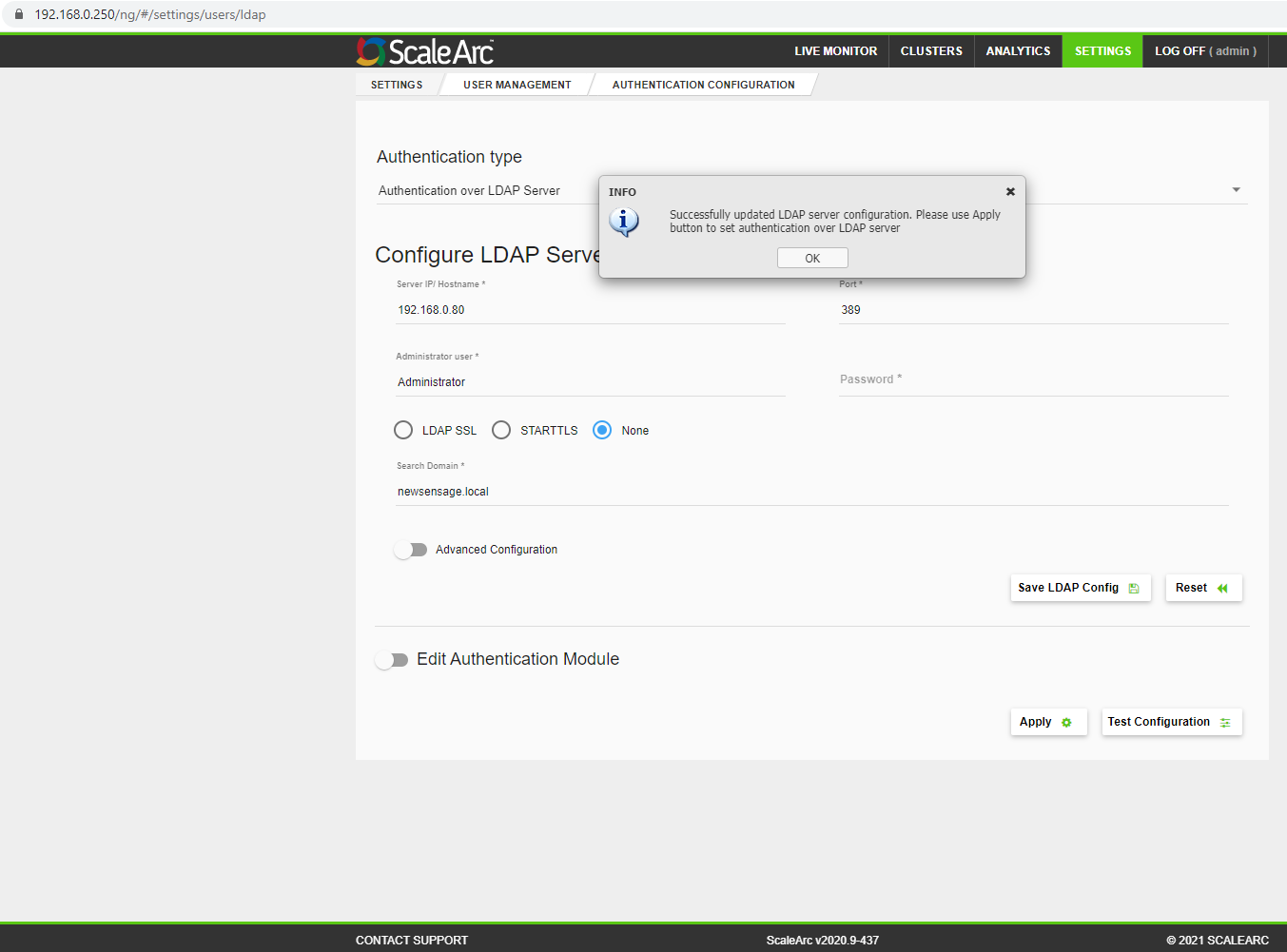
- User groups can be created in LDAP; after you configure the LDAP settings you can map LDAP user groups to roles in the ScaleArc policy.
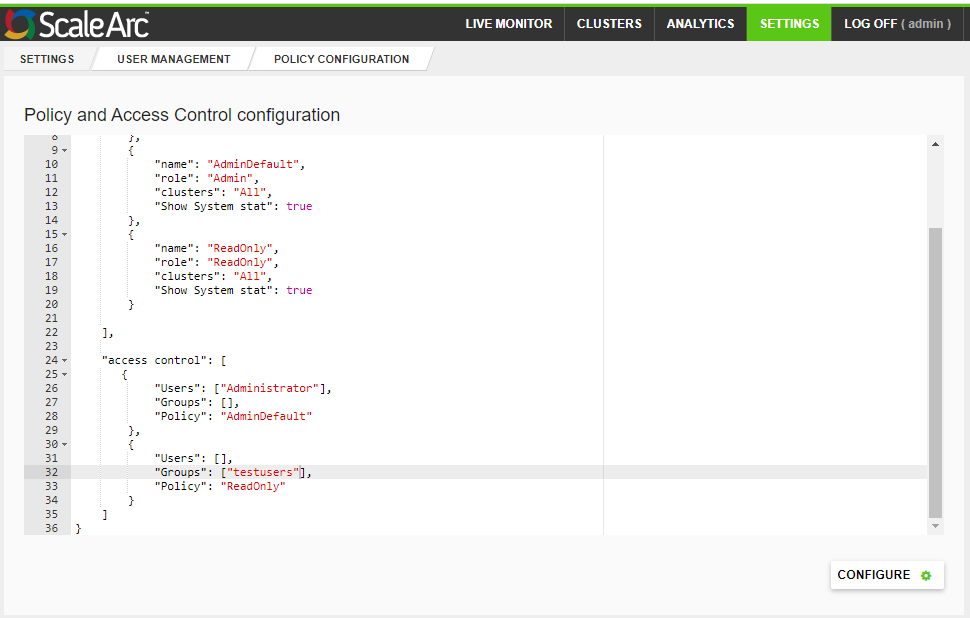
- Once LDAP is configured, only ScaleArc root UI admin account works as local user and rest all other users should authenticate through LDAP.
- The local ScaleArc administrator account continues to work after configuring LDAP and serves as a superadmin account.
- Note that if the LDAP Administrator account password expires then no LDAP user will be able to connect because ScaleArc can't connect to the LDAP server to authenticate the users. However, once the password for the Administrator user has been changed in the LDAP server, we just need to login to the ScaleArc UI, change the password as shown below, and save the configuration for the LDAP integration to work again. It is not necessary to log in via SSH to restore the LDAP integration.
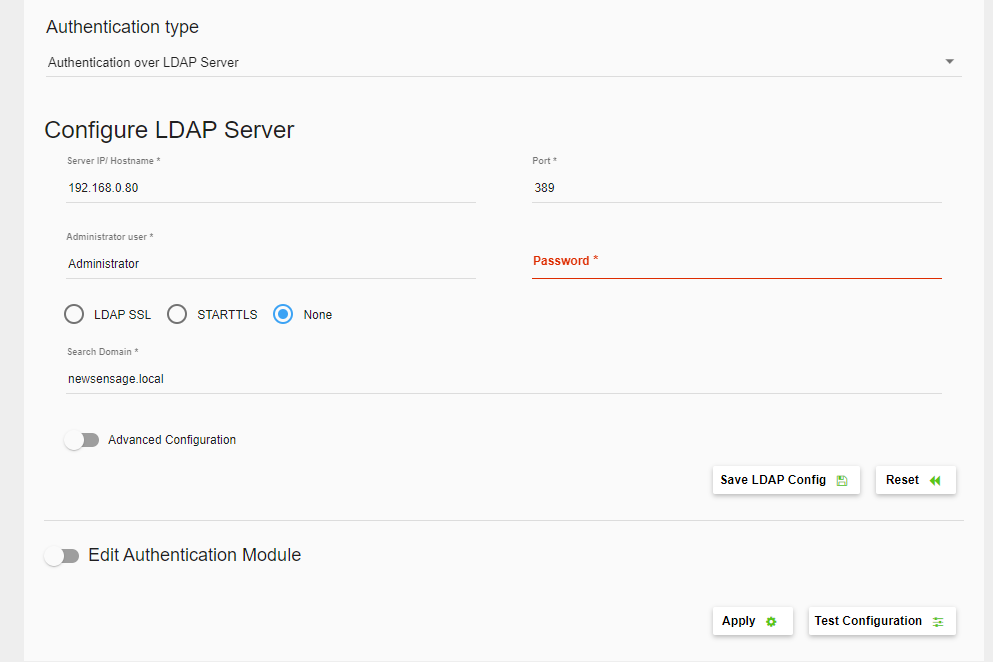
This is also mentioned in this KB article in the following paragraph in the Authenticate users over the LDAP server section
If the administrator's account password has an expiration date, the LDAP authentication from ScaleArc will fail past the expiration date. In this situation, the user needs to log into ScaleArc via the root user account and change the administrator password using the LDAP config page in ScaleArc. To avoid failure, update your administrator's password in ScaleArc when the password expires.
Comments
0 comments
Please sign in to leave a comment.